You may be a social media super-fan, but do you know the best security practices that should come with it? As the usage of sites like Facebook, Instagram, and TikTok increase, implementing safety measures is essential to protect your privacy and sensitive information.
As we become more connected, it’s important to stay aware of the security risks associated with these platforms. Whether you use social media as an individual or as a business, there are certain best practices that should be followed to ensure your safety online. Let’s take a look at some of the most important cyber security measures for social media users.
Passwords – The keys to your kingdom
Passwords are one of the most important security practices for keeping your life’s data secure. Weak passwords are easily guessed and can leave your account vulnerable to hackers. That’s why it’s important to:
1. Use long passwords (more than 12 characters) for each account. length is key to password strength, so the longer you can make a password, the better. If you worry about not being able to remember long passwords, check out the tip below about using “password managers”.

Photo by Jakob Owens on Unsplash
"It’s been a “super-fantastic” experience to see people learning and talking about security threats."
For just $325 USD, you can run a 6 week, automated program for gamified phishing awareness training and challenges. (Limited time offer. Normally valued at $999 USD)
Use Promo Code: 6WEEKS
2. Choose strong passwords that are difficult to guess that include a mix of upper and lowercase letters as well as numbers and special characters like @, #, $, %, etc.
3. Never re-use passwords between different websites or apps. If one site gets hacked, attackers may try passwords from the hacked site on other accounts.
Password managers
It’s a really good idea to use a password manager to keep track of all those long, unique passwords. Password managers make it easier for you to create, use and change passwords on many different sites. So you can make one unique, “primary password” that is long, and includes many characters, but allows you to have access to the rest of your unique, long and strong passwords. Remember to select a secure and reliable tool, rather than using your own “secret file” of passwords that could be stolen. Despite the recent LastPass data breach, it is still a very good idea to use a password manager. As long as your primary password is very long, it will be much less risky than re-using passwords between accounts.
Multi-Factor Authentication
Multi-Factor Authentication, is a great way to add an extra layer of security to each of your social media profiles. For example, you would be required to enter your password and a code that is sent to your phone number or an app you have downloaded on your phone. By turning on multi-factor authentication for each account, you now require two or more authentication factors to log in. So, if your password for one site is stolen, the attacker will still not have access to your app or texts for the other factor.
Social engineering & Phishing
What is social engineering?
Social engineering attacks are becoming increasingly prominent on social media. This is simply the term for attackers tricking you into providing valuable information such as credit card details, passwords, or confidential personal data; or convincing them to pay for something or to do something that helps the attacker, without them knowing it.
For example, many people and businesses are being impersonated on Instagram, Facebook or LinkedIn. You may see that an exact replica of a friend, peer, or business’s profile has started to follow you on the app. If you follow back or connect, you’ll most likely receive a DM that will start out casually, but eventually lead you to give private information or take some action, because we tend to put more trust in people we are connected to.
What is phishing?
Phishing is very similar to social engineering, but occurs when attackers use email messages to get you to take actions. Attackers will try to entice you into clicking on a malicious link or open a malicious attachment that could infect your computer with ransomware, or take you to a fake website to try to collect sensitive information like passwords.
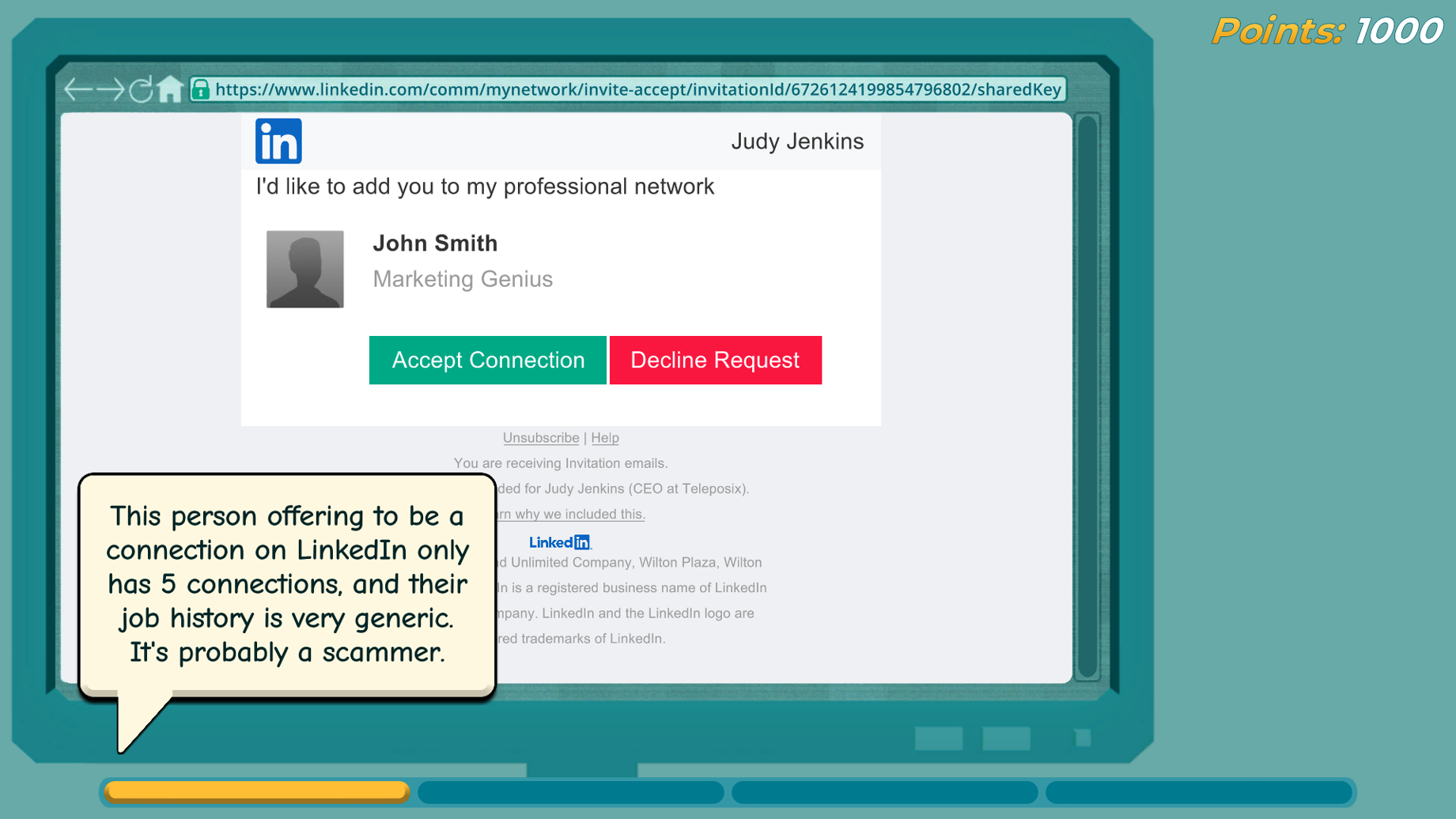
This is extremely common on LinkedIn. A connection will impersonate a friend, add you, and then ask you to check out their business or some interesting article through a website link, and send you a malicious link to get your information or give your computer a virus to take control of your computer.
What can you do to protect yourself and your employees?
Social engineers are getting so good that it’s almost impossible to see the difference between fake profiles and real ones. Always check the username (it will likely be only one letter off, or have relatively few connections whom you know). When in doubt, you should reach out to the friend or colleague via a separate text message, email or phone call, to clarify if it is really them. If it’s not, make sure to report the account and inform the person who is being impersonated.
The best safety methods for phishing messages are to not open links from people you don’t know, or whom you just connected with. However, it’s possible the link can come from an attacker impersonating somebody you know, as well, so you will want to double check their real identity. You can also search the “real” site they are claiming to send you, to so you can see if the website is real and if the URLs are the same.
The most valuable thing your employer can offer its employees to protect their personal and business accounts is education and practice, practice, practice. Employees should take the opportunity to practice identifying social engineering messages, so when a real one comes along they know what to do.
Protect your privacy
Facebook, Instagram, and TikTok are businesses that are trying to make money through advertisements, and don’t care as much about your privacy as you may think they do. Their privacy settings and agreements are constantly changing, to make it harder for you to prevent your information from being collected and sold to marketers. We recommend checking your privacy setting every 3 months to see if they are still set to something you are comfortable with.
You can also choose different levels of privacy on social media sites, to control how much information about you is shared with others about your. For example, you can use settings to control who can see your profile information (i.e., friends, friends of friends, or anyone else), what people can see (including location and when you are using the app), and what information from your posts, likes and shares is shown to others. Stand up for yourself by taking advantage of these features and only allowing what you are comfortable with.
The best security practice
The number one security practice we recommend for protecting yourself on any social media platform is: Having good general knowledge about cyber security risks and best practices. Knowing the strategies that different hackers use is essential for anyone who interacts with social media on a regular basis – whether for business or pleasure.
As an individual
As a casual user of social media, it’s important to understand how data is used and shared on these platforms so you can better protect yourself from potential threats. Educate yourself on how best to safeguard your accounts by reading up on the latest news in cyber security and staying up-to-date with new developments related to social media usage and privacy policies.
As a business
Employers should ensure their employees have the correct training that not only teaches them about potential threats, but allows them to practice engaging with them using interactive exercises. Cyber security training that is interactive and gamified allows for better knowledge retention and drives better overall participation from a team.

Click Armor’s unique social engineering and phishing exercises take you through many of the most common types of dangerous personal interactions. They allow each employee to interact with these realistic situations in a safe and fun environment, and to learn the right and wrongs before the real situation approaches and it’s too late.
Social media plays an integral role for productivity, social engagement and entertainment in modern life. However, it can be difficult for users—both individuals and businesses—to stay secure online with ever-evolving threats such as phishing scams and malicious software targeting their accounts every day. The best way to protect yourself is by having general knowledge about cyber security, choosing strong passwords for each account you have, and looking out for any suspicious emails before clicking on anything contained therein.
By following these simple steps, you can help keep yourself safe while still enjoying the benefits that social media provides!
Scott Wright is CEO of Click Armor, the gamified simulation platform that helps businesses avoid breaches by engaging employees to improve their proficiency in making decisions for cyber security risk and corporate compliance. He has over 20 years of cyber security coaching experience and was creator of the Honey Stick Project for Smartphones as a demonstration in measuring human vulnerabilities.


