As security breaches and attacks are on the rise, so are the security awareness news stories that come with them. How can these startling headlines be used in a positive way to educate your employees?
In our latest live Cyber Security Awareness Forum, we hosted a panel to discuss recent news stories and how to use them in your security awareness program.
Meet the panel:
Chris Kayser – Chris is the Founder and CEO of Cybercrime Analytics Ltd, a cybercrime consulting and research firm. Chris is currently researching the effects and targeting that cyber attacks have on different generations.
Michelle L. (ML) – Michelle is the Cyber Security Awareness Lead at Channel 4 in the UK. Channel 4 is a publicly-owned and commercially-funded UK public service broadcaster.
"It’s been a “super-fantastic” experience to see people learning and talking about security threats."
For just $325 USD, you can run a 6 week, automated program for gamified phishing awareness training and challenges. (Limited time offer. Normally valued at $999 USD)
Use Promo Code: 6WEEKS
Fletus Poston (FP) – A security champion, Fletus is a Senior Manager of Security Operations at CrashPlan®. CrashPlan® provides peace of mind through secure, scalable, straightforward endpoint data backup for any organization.
Ryan Healey-Ogden (RH) – Ryan is Click Armor’s Director of Business Development, he holds a passion for security awareness, education, and technology and how it relates to people.
And myself, Scott Wright (SW), CEO of Click Armor, the sponsor for this session. Now, let’s get to our discussion on timely news stories:
Security Bites
Don’t have time to watch the whole panel? Get exactly what you need with these security bites:
Security Bite: I’m an executive
- Is it a people or technology issue? – 23:00-25:50
- Stop with the blame! – 53:10-54:15
- Creating a safe space to ask questions. – 60:00-60:58
Security Bite: I’m a security awareness manager
- How executives like to receive information. – 13:04-13:30
- Talk about the positives, not just the negatives. – 29:05 – 30:05
- What organizations need to be aware of. – 48:40 – 49:50
Security Bite: I’m an individual
Which most recent news stories do you find useful for your security awareness?
CK: This didn’t make the news, although it has hit the news many times. I got a call from someone who I’m very close with. Her computer had been locked up and a person’s voice was screaming at her that they had taken over her computer and that she was not allowed to turn it off or they would destroy her computer forever.
It turns out, two days ago her computer got locked up and a phone number popped up, claiming to be Microsoft, and she called them. She let them on her system for some period of time. Which is how this person got access.
I want to get this story into mainstream media, because unfortunately this story is not unique. It is happening to a lot of people, particularly elderly people with little experience with technology.
FP: There’s the PayPal scam where they legitimately send you a valid invoice. And they win either way, because either you pay it or you click on the phone number in invoice email. The email doesn’t have PayPal’s number, it’s the adversaries number. When you call them, they walk you through the steps of using “Forget Password”. Then they log you out of your account and drain your bank account.
SW: There’s a story about a social engineering kill chain. Which was a phone scam that was conducted on a construction company that was impersonating a supplier and got them to actually pay a fair bit of money by convincing somebody that they owed money.
Then there’s a smaller story about Colorado State University that was hit and a lot of personal information was exposed as a result. It was a technical vulnerability, but we have to educate developers as well. Not all stories have to target individuals specifically.
ML: The LastPass breach is very interesting. It was a lot of social engineering and it happened on their home device.
How do you present real news stories to employees in your security awareness program?
FP: I set up an RSS Feed into a Slack channel for my security team as well as others who have interest in it. So, 24/7 they have articles coming in that they can review. And then an all channel where we can send messages on more popular articles and say, “Hey, you might have read this today. Here’s how it affects us here, how that affects you, and how it affects your family and friends.”
Then we have a general security culture/awareness channel, but we also cross post articles and put polls and stuff in there to apply there.
ML: I agree. An RSS Feed is great or you can have someone consistently send timely articles or updates on what’s going on in the industry. I think it’s also great to have a way to communicate with your cyber-targeted groups or your champions.
To go up higher, I see it can be a bit more difficult. So, I find it easier to send it directly to them, whether it be an article that you saw or a podcast – executives seem to love podcasts – and ask them how they want to share this information.
Where do you source your news stories?
CK: My first choice for news source for security stories is mainstream news, whatever stories are getting reported. How are they getting reported and how does it raise the awareness of the individual to how vulnerable they are?
Too often we separate organizations and individuals, but we have to remember that an organization is a group of people. When they go to work their mindsets don’t just change. It’s still the same mindset of how they use computers, how they use social media, how they communicate, what they click on, what they don’t click on. They’ll do that at work or elsewhere. By looking at mainstream news you can find out how relatable they find stories to their own lives.
RH: Sometimes mainstream news can sensationalize things or blow things up, but I think that’s how we can utilize it for good. I have experience in the education sector and teaching students cyber security, and one of my constants was using real life news stories and the top of everyday to engage conversations. It brings them into this world of paying attention to what’s going on and how they can solve their problems with real life examples.
SW: The process that I typically use if I’m trying to educate a particular team or organization, is: step one, I look at the mainstream news because those are the things that we just talked about that resonate with people that everybody kind of has heard of. And it’s easier to get them to focus on it rather than some obscure thing. But at the same time, most mainstream articles don’t include the details that we actually need to help people understand what they should do differently.
So, step two: I go and find something in Ars Technica or wired to look more deeply at how it actually happened and the vulnerabilities that allowed it to happen.
FP: I also would like to shoutout the SANS Internet Storm Center. They do a 5 to 7 minute podcast everyday recapping the previous news stories for the previous day. And you can start your day by just listening to it. Johanna Yohannes does a great job of picking 3 to 5 stories and just recapping them, giving you links. That’s a great one to start with because you can see what is getting traction from the SANS Internet Storm Center because they have honeypots, they are watching for this data.
ML: I love the 404 Security Not Found Podcast, Anna, one of the hosts, is brilliant. Then, I also love Security. Cryptography. Whatever. because it gets into the weeds on a lot of the technical stuff.
RH: For podcasts, Gerald Auger does one every morning 8-9am EST, it’s a great daily cyber brief. Basically he does a livestream everyday with lots of energy and I encourage my students to watch it everyday and follow along because it captures their attention.
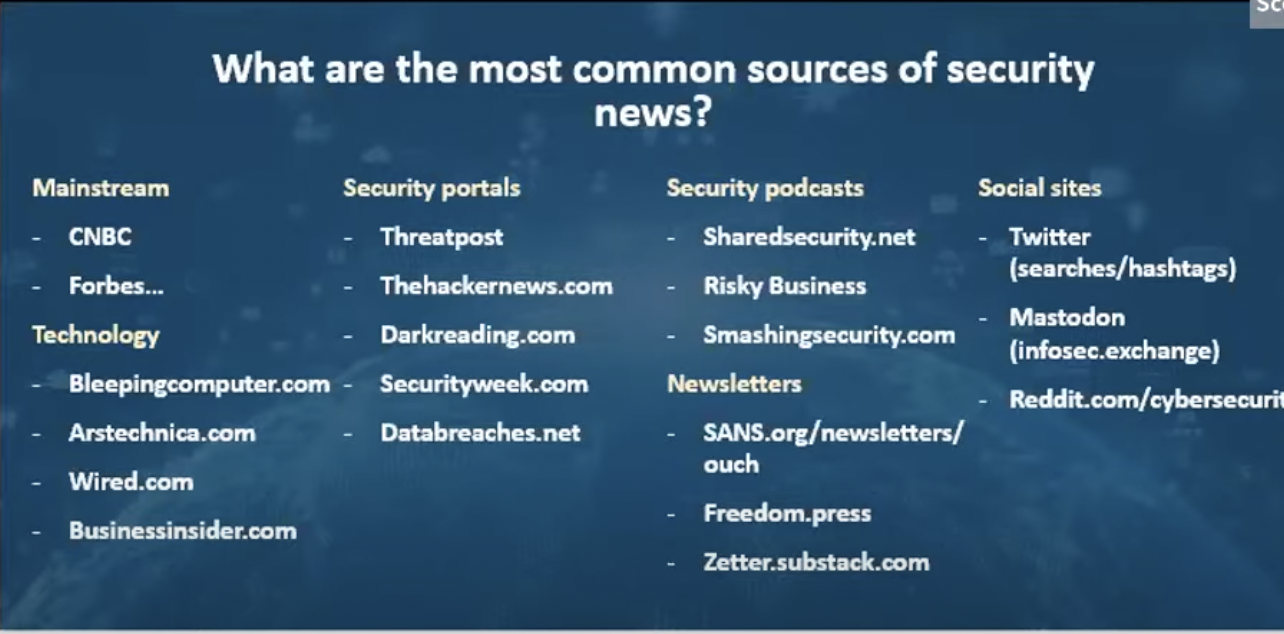
Based on our panel’s input we also shared this list of common sources of security news.
How do you know if stories are helpful to employees?
ML: I think it’s important to note that we don’t want to overwhelm or scare people, but we do want to keep them informed. And there’s a lot in the news at the moment. Things are really evolving quite quickly, and I think the risks to private individuals are actually increasing as much as they are to organizations. And I think that’s very important to get people to share things, by sharing things that will help them personally as well.
I think it’s just about asking and creating a safe space. If people feel like they are in a safe space they will feel comfortable saying, “I like this.” or “Hey, this wasn’t that helpful.”
SW: Something I learned when working on risk assessment 15-20 years ago was in every story you should identify the threats, assets, and vulnerabilities. If you can’t identify those things when you’re telling somebody a story, it’s pretty hard to tell them anything about what they should be doing differently or why.
FP: It’s the security culture. Are they eager to come to you with a news article that they found or something that they applied?
—
If we’ve learned anything from this panel today, it’s that we don’t need to be scared of the news. We can utilize it in a positive way, to engage and educate our employees, and encourage casual conversations and interest in cyber security. If you want more information about news sharing and current news stories, watch the full recording on our YouTube.
Click Armor is the first highly interactive security awareness platform, with engaging foundational courses and 3-minute weekly challenges that employees love. We offer content on everything from security basics, phishing and social engineering to passwords and privacy.
Even if your organization already has a solution, there’s a high likelihood that some employees are still not engaging and are exposing your systems and information to cyberthreats. Click Armor offers a special “remediation” package that complements existing solutions that don’t offer any relevant content for people who need a different method of awareness training.
Scott Wright is CEO of Click Armor, the gamified simulation platform that helps businesses avoid breaches by engaging employees to improve their proficiency in making decisions for cyber security risk and corporate compliance. He has over 20 years of cyber security coaching experience and was creator of the Honey Stick Project for Smartphones as a demonstration in measuring human vulnerabilities.


