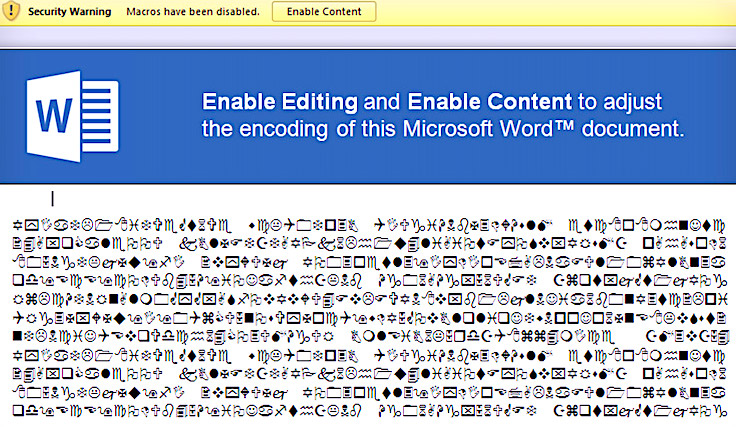
Most of us have learned not to enable macros in unexpected Microsoft Office documents. But there is a new malware attack that uses some less obvious social engineering tactics to get people to allow macros to run.
Attackers are looking for more effective attacks, as users learn not to enable embedded macros
Attackers have often used embedded malicious macros into Microsoft Office documents, hoping the recipient of a phishing email clicks on the button to Enable Macros. This can allow an attacker to use more sophisticated methods to get their malware installed on a computer. However, it’s less likely to work these days, now that most users have been taught not to “Enable Macros” if they see the dialog box that pops up when they open a document.
Phishing attacks now use a document’s text content to trick users into enabling macros through DDE
While it’s much more complicated for an attacker to implement, there is a way that is proving to be more effective for them to trick recipients of a phishing attachment to enable enough privileges to enable them to run their own macros. It involves putting a convincing notice at the top of the Office document that looks legitimate, and which tells the user they need to “upgrade” or “convert” the document to a format that works with their current version by clicking the Enable Editing and then Enable Content buttons displayed by Microsoft.
This approach may appear to be requesting a less threatening action that is required in order to properly view the document. In fact, the rest of the document’s content, after the upgrade notice may appear as improperly formatted content, adding to the plausibility that the document needs to be converted.
The technical actions that occur once the user clicks the “Enable Content” button is very convoluted, but involves enabling Dynamic Data Exchange (DDE). This allows the Word document to download a remote excel spreadsheet and create automated instructions that eventually disable the macro warning, and execute maliciously coded macro.
Keeping end-users aware of new social engineering attacks
It’s a never-ending game of cat and mouse, where attackers find new ways around security technology. All technologies have limitations, and exploiting them can usually done by taking advantage of a user whose behavior can be manipulated.
Click Armor’s gamified learning approach works for phishing, as well as social engineering attacks, by engaging users to learn and then using simulation exercises to let them practice making good risk decisions in a safe environment.
If you are looking for a better way to strengthen end-user awareness again improve their defensive skills against phishing and social engineering, please book a call with us by using the button below.