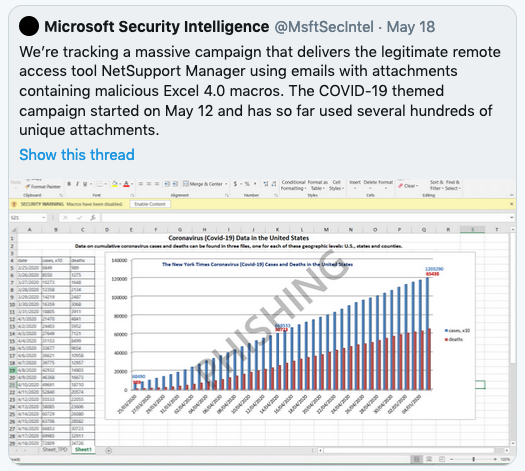
Why attackers who infect your system may try double dipping if you don’t pay them. Another reason to avoid ransomware at all costs.
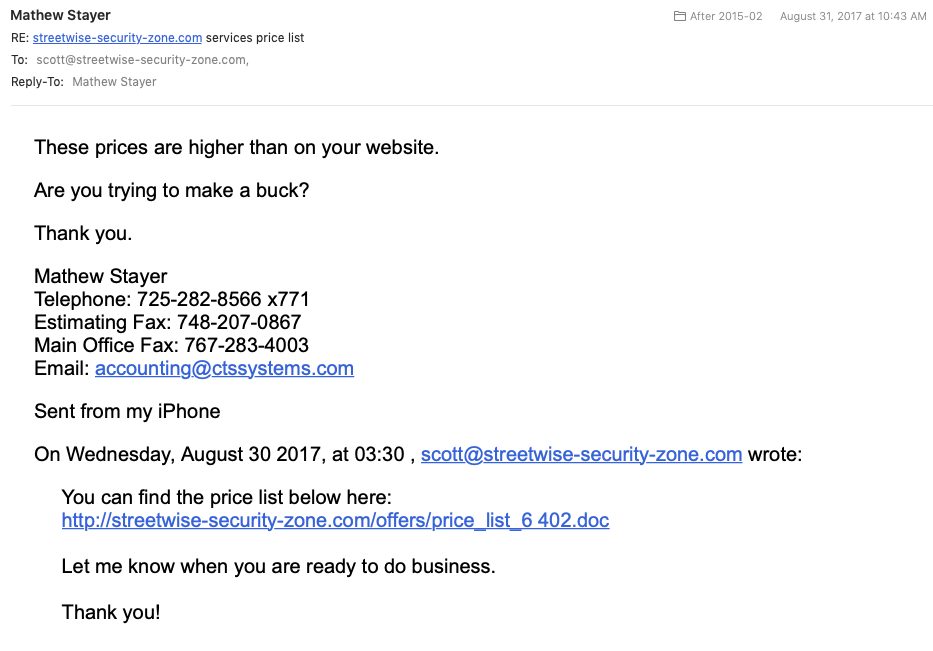
When hackers attempt to hijack your email account, there may be some clues that will tip you off. But with the right conditions, an attacker may be able to reset your email password and access many accounts you have access to. In this example, an engineer in San Francisco lost $100,000 in crypto currency this way.
Big Data is having a big impact in business, and its privacy implications can affect both companies and their employees.
Did you know that many SMART devices that are part of the Internet of Things are built with weak passwords that can’t be changed? This is a dangerous product flaw, and cyber attackers are now hacking millions of unprotected devices that are exposed to the Internet.