Executive Summary: The short answer to this question is that “phishing” is an opportunistic email attack that targets many people with a “false-premise” (or lie) to trick at least some of them into take an action for the attacker’s benefit. The attacker doesn’t really know who will fall for it. However, a “spear-phishing” attack targets key individuals or groups of people much more precisely, to achieve a higher value goal, and uses more elaborate deceptions that exploit the victim’s trust and emotions, based on what the attacker knows about them. This article explains in more detail how phishing and spear-phishing attacks differ.
Why are phishing and spear-phishing such a problem?
“Phishing” and “spear-phishing” are the most common causes of corporate security breaches. A Trend Micro report highlighted the fact that 91% of cyber attacks begin with a spear-phishing email.
You may already know that phishing messages try to trick people into clicking on links or attachments in emails. But you might be surprised at how much of a disconnect there still is between how people are being targeted in phishing attacks and how well they are able to defend against those attacks. According to Beauceron Security’s latest industry survey of over 20,000 individuals, 12% of the respondents did not know what the term “phishing” means.
It’s logical to assume from this finding that an even higher percentage of people probably don’t know what the term “spear phishing” means. So, if at least 10% of individuals aren’t even aware of what phishing is, the business world has a huge vulnerability, because security technologies aren’t able to detect and block every phishing threat.
In fact, data from Click Armor’s own “Can I Be Phished?” online phishing self-assessment indicates that 90% of individuals who have tried the challenge mis-identify at least one in ten potential phishing messages.
Opportunistic versus targeted emails
You can think of “regular phishing” as an opportunistic kind of attack, where the attackers don’t really care who the victims are; only that they can trick enough people to make it worth their while. “Spear-phishing” is more of a targeted attack, where the attacker has a specific goal in mind, and will spend more time setting up the attack to be successful against specific victims.
As an analogy, think of the difference between a hustler that opportunistically cheats people in Three-card Monte card scams, and the elaborate plots and setups in movies like “The Sting”, “Oceans Eleven” or “Inception”. (All three of these are rated in the top 10 “con artist” movies by “screenrant.com”.) Both methods use various kinds of deception techniques. But the higher value the target is, the more effort it takes to succeed, because they usually have stronger defenses in place.
In both regular phishing and spear-phishing messages, their subject lines and bodies and almost always involve impersonation of somebody the target victim trusts. The difference between the two is mostly in how much effort the attacker puts into their research, and the creation of situations where the target will not suspect that they are being tricked.
How do you know if you’re being scammed in a simple phishing attack, or part of a more evil plot?
Opportunistic attacks are often easy to spot because something just doesn’t look right, and the usually message comes unexpectedly. But it’s not always easy to tell if a message is a spear-phishing attack, and sometimes it’s almost impossible to know at the beginning of an encounter. A basic phishing attack may have a simple request (“Is this really you?”) or notification message that plays on some emotion like fear (“This is your final notice!).
The basic phishing attacker doesn’t need to do much research to be successful, and they don’t really know which victims will fall for it. Phishing attackers usually play a numbers game, where some people will react without thinking, going to a website link or triggering a malware download; and eventually, the victim may enter sensitive information like a password or credit card number, or an unprotected computer will become infected with a virus or ransomware.
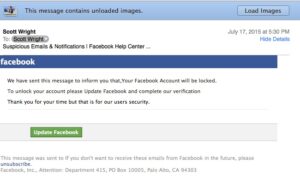
The attacker may, however, put signficant effort into making a message appear to be from a commonly trusted sender, such as major websites like Facebook, Apple or Google. These aren’t really targeted at specific people. So, you may see a notification from Apple, even though you don’t use any Apple products or websites. That would be an obvious clue that it is an opportunistic attack.
The message shown here is a typical, opportunistic phishing message.
Most phishing attacks – regular phishing and spear-phishing – have some recognizable characterisics in different elements of the message. The main elements of any phishing message are the “emotional appeal” or “hook”, the “sender information” and usually a “hyperlink” or “attachment” that triggers an exploit to infect the computer or try to gather information from the victim through an online form. Each element may have clues that can reveal something useful to you in analyzing whether a message is suspicous or not.
Why are spear-phishing messages harder to detect?
There are usually some people who will fall for a basic phishing attack in most organizations, especially if there isn’t a robust, continuous phishing awareness program. Good security software will stop most basic phishing messages based on commonly known traits, but not all of them, since attackers change methods to avoid being detected. In fact, attackers often test their latest messages against the best security software until they are able to get through undetected in their own tests.
You can usually analyze most phishing attacks to find clues in their sender information, as well as hyperlinks or attachments. Sometimes their message content or subject lines will also provide clues about whether or not the message should be treated as suspicious.
In spear-phishing, the main elements of a given email message are the same, but the attackers have a much better idea of whom they are targeting with more elaborate phishing messages, and a much higher expectation of what they want to gain from a successful attack. They key is that a targeted can leverage the trust and emotions of the victim in ways that make them less likely to actually check for the clues. The clues can also be harder to spot than in basic phishing messages, especially if the message resembles a normal communication.
How do spear-phishing attackers make their messages so convincing?
Just like in popular bank heist movies, there are often multiple steps in an attack, and multiple intermediate targets. The first step in a spear-phishing attack rarely even involves the attacker doing anything suspicious. Since the spear-phishing attacker wants to appear believable to you (assuming you are their target), their first step is to do some research.
We all leave a trail of information behind in almost everything we do, and that’s where the spear-phishing attacker will start. The easiest things for them to learn about you might be from Google searches or searches on social media, to see if your profile is public, and if you have made any public posts, shares or likes.
These bits of information that are publicly accessible can tell an attacker some basic information about you, and sometimes, if you “overshare” or are a somewhat public figure, they can learn a lot about you and the people you normally interact with. People don’t expect that anyone would bother harvesting their social media activities. But that’s exactly what attackers do very easily, and very well.
This kind of research is called “profiling”, and the information gathered this way is called “Open Source Intelligence” or OSINT, for short. In decades past, before social media existed, profiling was often done by attackers who literally searched through the trash bins outside of office buildings. This method was called “dumpster diving”, and even today, dumpster diving is still used to gather information that will help spear-phishing attackers in targeting their victims based on real information they have found that was unprotected. This is why shredding of sensitive office documents is so important.
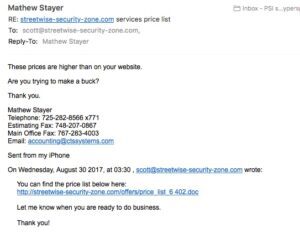
I once received a very well-crafted message that clearly targeted my business, accusing me of having tried to rip off the sender by quoting him higher prices than were in a price list I had sent him. The documents and links used in the message had the name of my business and its proper domain in the “anchor text” – an important term we teach you about in Click Armor’s phishing awarenes training. The tip off for me was that I had never had a price list for that business, and therefore, I could never have sent him one! So, the attacker hadn’t done quite enough research to convince me to click on the link, but I would still call the message shown here a very good spear-phishing attack.
Softening you up with a pretext
Once an attacker has enough information about the people their target trusts, they may create intermediate phishing attacks on those individuals, to build a more elaborate scheme or “pretext”. For example, if the attacker can learn about a company that supplies the victim, they can identify people in the supplier organization, and try to learn more about the victim, or get an introduction to the victim from somebody they trust.
This is called a “stepping stone” attack, and it works very well because most people don’t believe that they are giving the person any information of value that could be abused, or that an attacker would go to so much trouble, just to get an introduction. By the time the target victim gets the spear-phishing attack in this case, they are likely to be acting mostly on the trust that they have in the people whom they “believe” they are dealing with.
Whaling, ice-phishing and watering-holes
There are also variations on spear-phishing attacks, such as “whaling”, “ice-phishing” or “watering-hole” attacks. Whaling attacks target senior executives who may have higher levels of authority and access than other staff, making it more worth-while for an attacker to do research and create more elaborate pretexts.
Ice-phishing attacks take advantage of corporate webmail accounts that have been hacked, just to get access to an account inside the corporate perimeter. The attacker then uses the compromised account to impersonate people within an organization, allowing them to launch attacks on larger targets within the organization.
Watering-hole attacks are messages posted in forums dedicated to subjects that the target victim is known or likely to visit frequently, in hopes of enticing them to engage in discussions to begin a trusted relationship that can later be exploited with spear-phishing emails.
Spotting any kind of phishing attack requires a disciplined routine
The rules of basic phishing email analysis remain basically the same, regardless of whether you are facing a “phishing” attack, or a “spear-phishing” attack. It’s just that you are less likely to follow those rules with somebody you trust. This is why it is extremely important to be always on the lookout, and instincitvely ready to defend against messages that seem a little unusual or inconsistent, or from people you have only recently connected with.
Sometimes it is virtually impossible to spot a well-crafted spear-phishing attack, and you might wonder “what’s the point in trying, if they are so good, and nothing is going to stop them”. But the important thing to recognize is that with 20% of employees who don’t know what phishing is, let alone how to analyze a potentially suspicious messages, the attackers don’t really need to go to that much trouble to create a convincing attack.
So, as long as you are in the habit of always checking, you can spot many of them, which will reduce your risk a great deal. Understanding how attackers use social engineering techniques like profiling and pretexting is important for catching the more elaborate attacks where you might be a target, or you might just be a stepping stone to a larger “spear-phishing” attack.